This is very much a work in progress and I'm relatively new to offensive security in general so if you see something that can be improved please open an issue or PR with suggested changes.
Cloning for development
Outside of your gopath
git clone https://github.com/leobeosab/sharinganInstalling
go get github.com/leobeosab/sharingan/cmd/sharingancliDependencies
- NMap
- Go
Usage
Note
Order matters when it comes to flags it must be
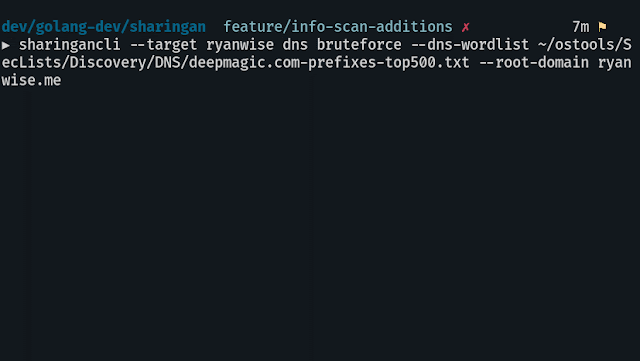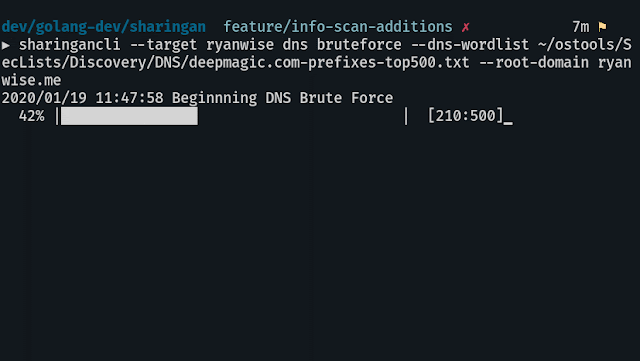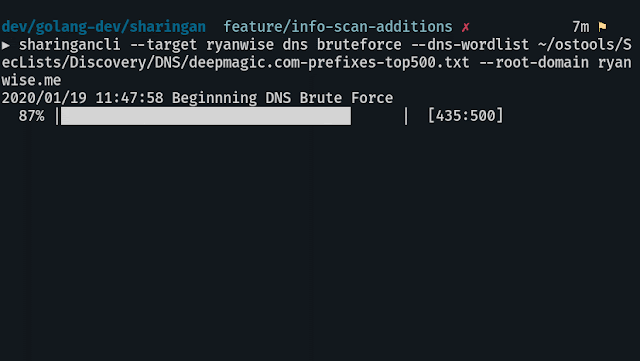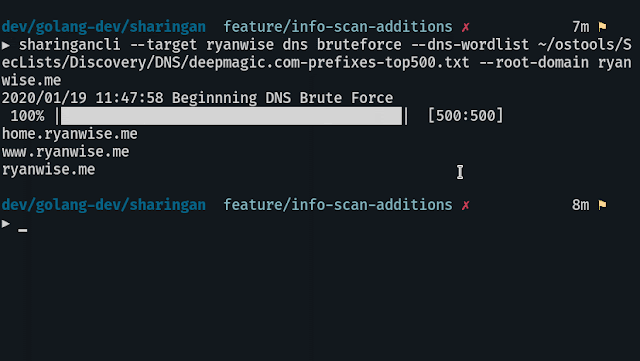
sharingancli [globalflags] command [commandflags] if this isn't a wanted feature I can change it but I like how clean it isDNS
bruteforce
DNS busts the target with a wordlist you provide
sharingancli --target targetname dns --dns-wordlist ~/path/to/wordlist --root-domain target.comaddsubs
Adds subdomains to the program's storage from stdin using pipes
cat subs | sharingancli --target targetname dns addsubsScan
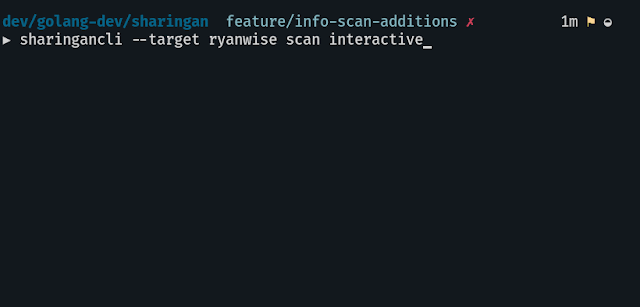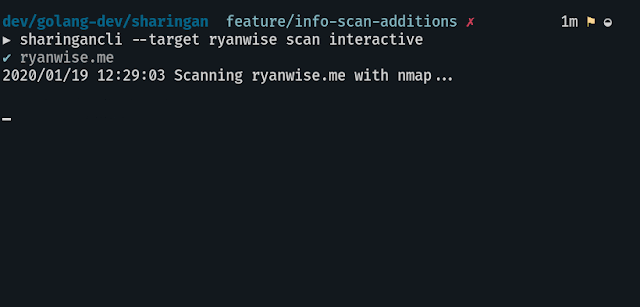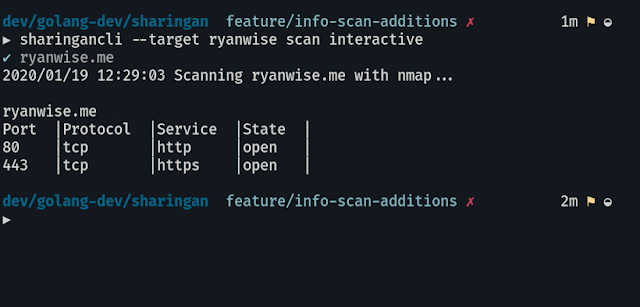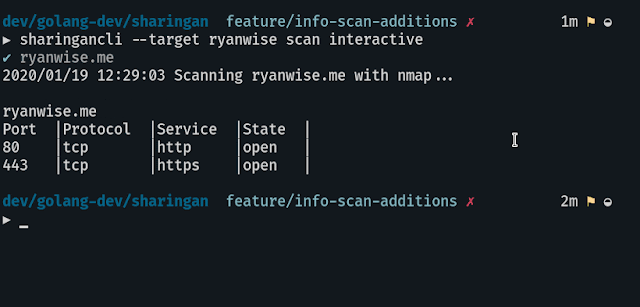
Scans all hosts available that were stored in target using nmap
sharingancli --target target scaninteractive
Scan a single host from list of subdomains stored in target
sharingancli --target target scan interactiveinfo
domains
Outputs all domains as a list in stdout
sharingancli --target target info domainsFeatures to come
- Dir brute forcing -- Currently being worked on
- JSON and regular file exports
- Automated scans through a daemon?
- add a way to do SYN / -sS scanning [ must be root so it presents a challenge ]
- Possible Web ui / html export
via KitPloitRelated news







No comments:
Post a Comment